IAM Terms
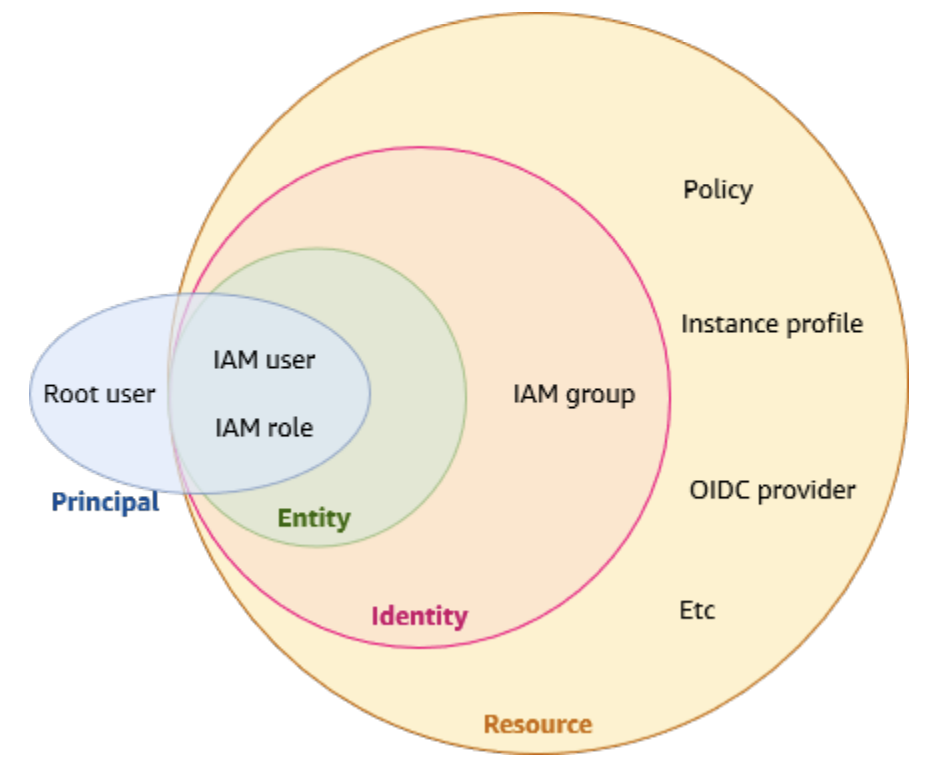
IAM Resource
The IAM service stores these resources. You can add, edit, and remove them from the IAM console.
- IAM user
- IAM group
- IAM role
- Permission policy
- Identity-provider object
IAM Entity
IAM resources that AWS uses for authentication. Specify the entity as a Principal in a resourcebased policy.
- IAM user
- IAM role
IAM Identity
The IAM resource that's authorized in policies to perform actions and to access resources.
Identities include IAM users, IAM groups, and IAM roles.
Principals
An AWS account root user, IAM user or an IAM role that can make a request for an action or
operation on an AWS resource. Principals include human users, workloads, federated users and
assumed roles. After authentication, IAM grants the principal either permanent or temporary
credentials to make requests to AWS, depending on the principal type.
-
Human users are also known as human identities, such as the people, administrators,
developers, operators, and consumers of your applications. -
Workloads are a collection of resources and code that delivers business value, such as an
application, process, operational tools, and other components. -
Federated users are users whose identity and credentials are managed by another identity
provider, such as Active Directory, Okta, or Microsoft Entra. -
IAM roles are an IAM identity that you can create in your account that has specific permissions
that determine what the identity can and can't do. However, instead of being uniquely
associated with one person, a role is intended to be assumable by anyone who needs it.
IAM grants IAM users and the root user long-term credentials and IAM roles temporary
credentials. Federated users and users in AWS IAM Identity Center assume IAM roles when they
sign-in to AWS, which grants them temporary credentials.
As a best practice, we recommend that you require human users and workloads to access AWS resources using temporary
credentials.